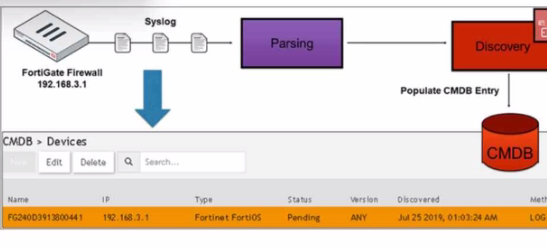
Refer to the exhibit.
Correct Answer:
D
Discovery Methods in FortiSIEM: FortiSIEM can discover devices using various methods, including syslog, SNMP, and others.
Syslog Discovery: The exhibit shows that the FortiGate device is discovered by FortiSIEM using syslog.
Syslog Parsing: The syslog messages sent by the FortiGate device are parsed by FortiSIEM to extract relevant information.
CMDB Entry: Based on the parsed information, an entry is populated in the Configuration Management Database (CMDB) for the device.
Evidence in Exhibit: The exhibit shows the syslog flow from the FortiGate Firewall to the parsing and discovery process, resulting in the device being listed in the CMDB with the status 'Pending.'
Reference: FortiSIEM 6.3 User Guide, Device Discovery section, which explains how syslog discovery works and how devices are added to the CMDB based on syslog data.