Based on the Fortinet FCSS - Network Security 7.6 documents and the analysis of the provided exhibits, here are the verified answers.
Questio ns no: 93
Verified Answer: B
Comprehensive and Detailed Explanation with all FCSS - Network Security 7.6 documents:
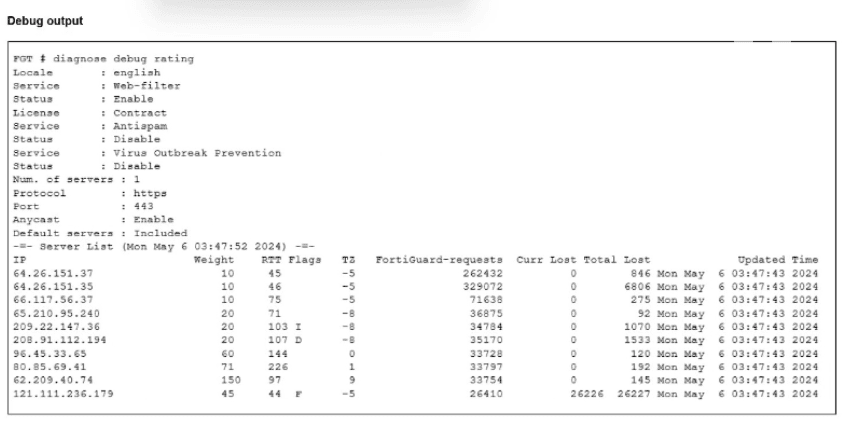
To determine which IP address was resolved via DNS, we must interpret the Flags column in the diagnose debug rating output provided in the exhibit:
Analyze the Flags:
Flag I (Initial): This flag indicates the IP address that was returned by the DNS query when resolving the FortiGuard FQDN (e.g., service.fortiguard.net). It acts as the 'seed' or initial contact point.
Flag D (Discovered): This flag indicates servers that were not resolved via DNS but were learned dynamically from the FortiGuard network during protocol exchanges (server lists sent by the initial server).
Flag F (Failed): Indicates a server that the FortiGate tried to contact but failed.
Examine the Exhibit:
The IP address 209.22.147.36 has the flag I next to it.
The IP 208.91.112.194 has the flag D.
The IP 121.111.236.179 has the flag F.
Conclusion:
Since the question asks specifically for the IP obtained when resolving the name, we look for the 'Initial' (I) flag. Therefore, 209.22.147.36 is the correct answer.
Comprehensive and Detailed Explanation with all FCSS - Network Security 7.6 documents:
The error message iprope_in_check() check failed, drop in a debug flow indicates a failure in the Local-In Policy check. This function determines whether traffic destined to the FortiGate itself (management traffic or local services) is allowed.
C . The packet was dropped because the trusted host list is misconfigured:
Reason: If an administrator has configured Trusted Hosts (limiting administrative access to specific source IPs), and a packet arrives from an unauthorized IP, the iprope_in_check function will reject it immediately to protect the device.
D . The packet was dropped because the requested service is not enabled on FortiGate:
Reason: The most common cause for this error is that the destination interface does not have the specific service (e.g., SSH, HTTPS, PING) enabled in its set allowaccess configuration. If the service is not listening/allowed on that port, the input check fails and drops the packet.
Why other options are incorrect:
A: If traffic is dropped by a standard firewall policy (traffic passing through the FortiGate), the debug message is typically denied by policy x or no matching policy, not an iprope (Input Property/Policy Enforcement) failure.
B: A routing issue where the source is unreachable results in a Reverse Path Forwarding (RPF) failure, typically logged as reverse path check fail, drop.
FortiGate Security 7.6 Study Guide (Security Fabric & FortiGuard): 'In diagnose debug rating, the 'I' flag stands for Initial, which is the IP address resolved by DNS. The 'D' flag stands for Discovered.'
Questio ns no: 94
Verified Answer: C, D
FortiGate Troubleshooting Guide (Debug Flow): 'The message iprope_in_check() check failed indicates the packet was denied by the Local-In policy, often due to missing allowaccess settings or Trusted Host restrictions.'