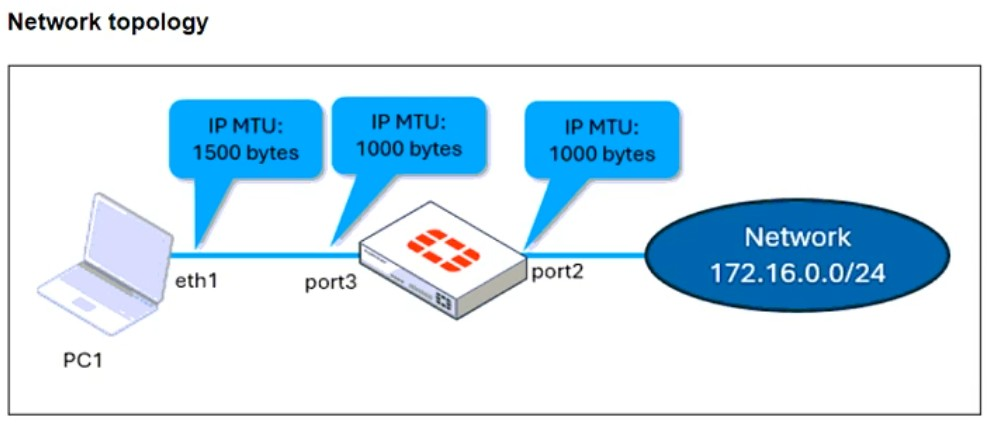
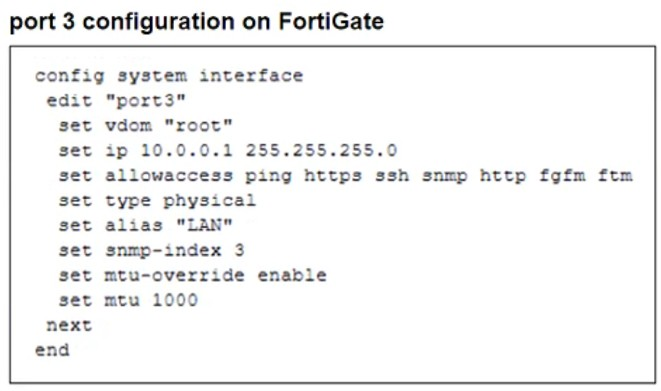
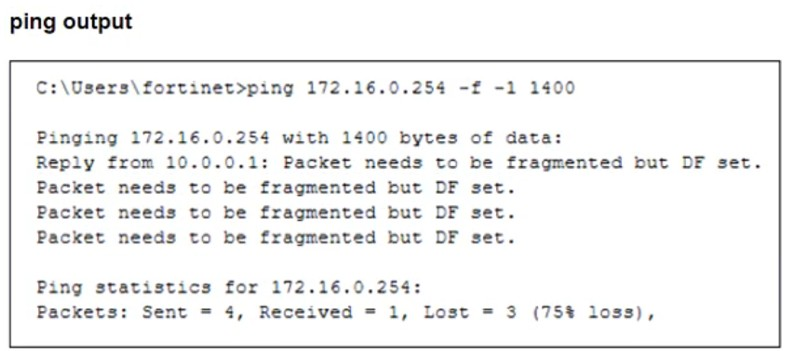
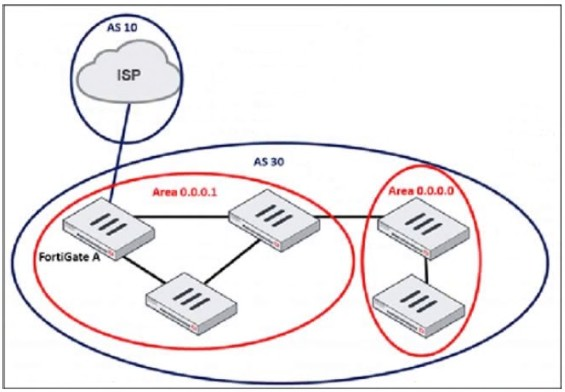
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
Correct Answer:
A, D
According to the FortiOS 7.6 Infrastructure study guide and High Availability (HA) documentation, FortiGate units in an HA cluster use a virtual MAC address to ensure seamless failover. The structure of this virtual MAC address is strictly defined by the Fortinet HA protocol.
For a standard HA cluster, the virtual MAC address format is 00:09:0f:09:<group-id_hex>:<vcluster_port_hex>. However, when VDOMs are enabled, the virtual MAC address prefix changes to e0:23:ff to accommodate the additional complexity of multiple virtual domains. Therefore, the prefix e0:23:ff in the suspicious MAC address e0:23:ff:fc:00:86 confirms that the packet originated from a cluster with VDOMs enabled (Option A).
Regarding the interface identification, the last byte (86) is calculated as follows:
The 0x80 bit indicates virtual-cluster 2 (vcluster 2). Since $0x86 = 0x80 + 0x06$, we know the packet is from vcluster 2.
The remaining value 0x06 represents the interface index. In FortiOS, the index starts at 0 (port1 = 0, port2 = 1, port3 = 2, port4 = 3, port5 = 4, port6 = 5, port7 = 6). Therefore, the index 6 corresponds exactly to port 7 (Option D).
The fourth byte (fc) represents the HA Group ID (252 in decimal). While this is indeed lower than 255, the specific logic of the virtual MAC composition in a VDOM-enabled environment points specifically to the port identification and vcluster status as the primary diagnostic conclusions.