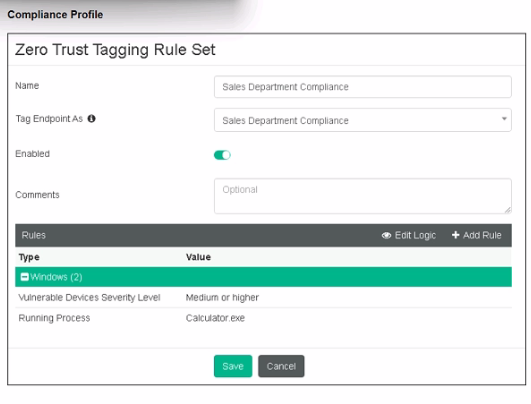
Refer to the exhibit.
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
Correct Answer:
B, D
Observation of Compliance Profile:
The compliance profile shown in the exhibit includes rules for vulnerability severity level and running process (Calculator.exe).
Evaluating Actions for Compliance:
To make the endpoint compliant, the administrator needs to ensure that the vulnerability severity level is medium or higher is patched (D).
Additionally, the Calculator.exe application must be running on the endpoint (B).
Eliminating Incorrect Options:
Enabling the web filter profile (A) is not related to the compliance rules shown.
Integrating FortiSandbox (C) is not a requirement in the given compliance profile.
Conclusion:
The correct actions are to run the Calculator application on the endpoint (B) and patch applications with vulnerabilities rated as high or above (D).
FortiClient EMS compliance profile configuration documentation from the study guides.