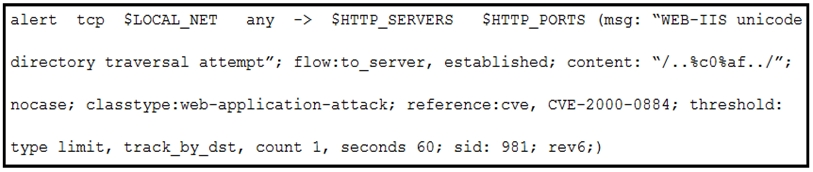
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?
Correct Answer:
B
To determine the correct script, we evaluate the following requirements:
The script must search for the IP address 192.168.100.100.
The output should be written to a file named parsed_host.log.
The matching lines should be printed to the console.
Analysis of the options:
Option A: Correct IP regex used and correct output filename, but reads from parsed_host.log instead of a source log file like test_log.log (not ideal for initial parsing).
Option C: The IP address used is 192.168.100.101 instead of 192.168.100.100 --- incorrect.
Option D: Same IP address and logic as Option B, but uses print statement without parentheses, which is not valid in Python 3 unless using Python 2 --- not ideal.
Option B:
Uses correct IP: '192.168.100.100'
Reads from test_log.log (presumably the source log file).
Writes to output/parsed_host.log.
Prints each matching line and writes to output file --- satisfying all conditions.
CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on 'Investigating Host-Based Evidence and Logs' emphasizes scripting log parsing tasks using Python's regex and file I/O for filtering artifacts like IP addresses. Scripts should ensure proper source log input, pattern matching, result redirection, and optional output logging for forensics analysis.
ChatGPT said: